
All About Browsers , DNS , DOM, HTTP Exchange, HTTPS and Malware
This is an article regarding browsers and other few important topics related to WEB-
Browsers

- These days, browsers have many functionalities, yet information retrieval from the Web still remains its primary one. Browsers do so by sending a request to a server demanding a piece of content, e.g. an HTML file, a video, or a PDF, and then presenting it to the end user in the browser window. While for you it’s enough to simply type in a URL into the protocol field, much happens under the hood. When wishing to access an online resource, we usually type in a URL, a Universal Resource Locator, such as gitgab.org/aws-training into the browser. Browser is an application program that provides user to access and interact with all the information available on the internet. All URLs have three main parts: a protocol, a domain name, and a path. Domain name is simply the name of the website. You can go to a domain registrar, purchase a domain name, as we have bitdegree.org, and register it so only you can use it. A path is usually, well, a path to a file or page on your website. For example, if you add /courses to the end of our bitdegree.org domain, the browser will immediately lead you to our course directory.
- A protocol is always placed at the beginning. It indicates which method of data transfer should be used. The protocol is usually referred to as the “language” between your browser and the web server. The most commonly used ones are HTTP, HTTPS, and FTP.
DNS ( Domain Name Service)
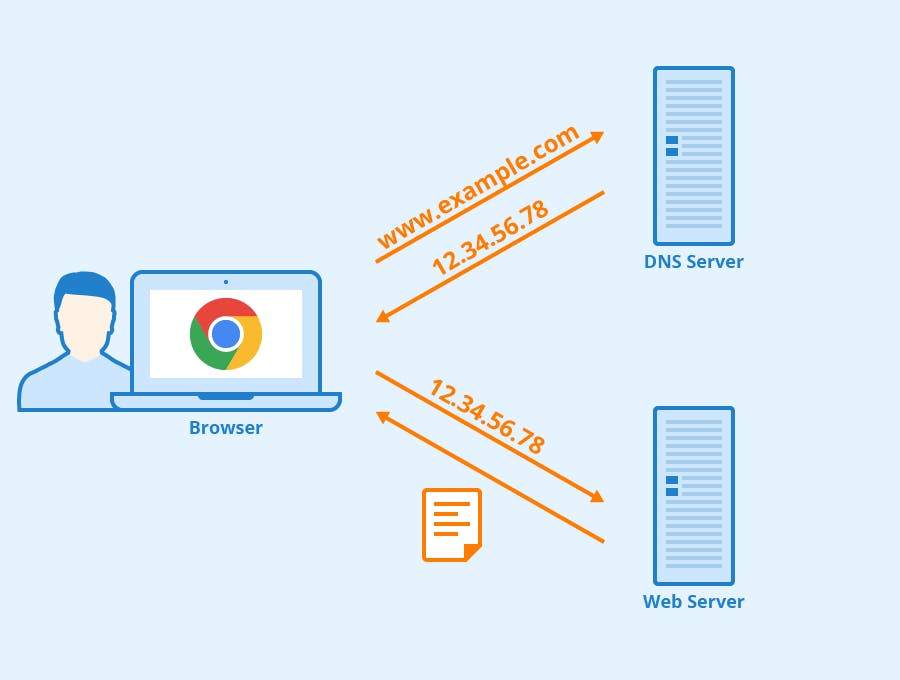
- The DNS is like the Internet’s phonebook: next to each name, there’s a corresponding number. DNS resolves the domain name into an IP address of the web server holding the asset. Domain name is simply the name of the website. You can go to a domain registrar, purchase a domain name, as we have ganzer.org, and register it so only you can use it. So if our name is ganzer.org, 104.26.2.80 is the website’s numeric computer-friendly counterpart. The domain name is a human-readable form of an IP address. To get the computer version, your browser brings a URL request to a Domain Name Service (DNS).
DOM ( Document Object Model )
- When the website’s HTML file does finally reach your web browser, its main role becomes interpreting the data received. After all, what it receives is nothing more than a binary stream of information in the shape of text. Once your browser loads the website, it also creates a DOM, or a Document Object Model. The DOM is a representation of the page in a programmable and standardized interface, used specifically for HTML and XML files.
- When your browser reads the HTML file, it creates a JavaScript object, called a node, for every HTML element it finds. This is called rendering. Having created all these nodes, it then shapes a tree-like structure displaying the relationships between all of them.
Meaning of DOM term wise
Document: any transferrable file, be it text, image, or HTML code. In the context of the DOM, document refers mainly to HTML files, e.g. a web page.
Object: data inside of your HTML file. For DOM, every HTML tag equals an object.
Model: the layout or a representation of your objects, displaying object-oriented relationships.
HTTP Exchange
- So, let’s take a step further and look into HTTP (Hypertext Transfer Protocol). HTTP is an Internet protocol that shapes online data exchange requests when fetching resources.
- Being a client-server protocol, its requests are typically initiated by the web browser (or another end user-agent) whenever it needs to display HTML code, images, videos, or other content. Once the servers receive the HTTP request, they send out a response containing the requested data.
HTTPS or HTTP-Secure
- While HTTP is the typical language used between browsers and websites, HTTPS adds an additional layer of security by encrypting communications. Previously, HTTPS was mainly used for websites handling sensitive data, e.g. banking details or social security numbers. Today, using it is common practice, even for pages without login functionality. It’s so common that most browsers will flag HTTP websites as “not secure”.
- To understand it better, think about an HTTP request: it’s simply lines of text sent over the Internet. HTTP websites do not protect this text, which means that, using free software, anyone anywhere can reach and read it. These requests can include submitted personal information, which malicious hackers could easily re-use for their own gain.

- HTTPS adds a padlock on these communications, encrypting them with a TLS/SSL certificate.
- Technically, it’s still the same protocol, just with an additional layer of security. Transport Layer Security, or TLS, uses public and private keys to scramble the HTTP request and makes it readable only to those with the necessary session keys.
- TLS is an updated version of SSL (Secure Sockets Layer) and is currently considered the industry standard for website security.
MALWARE

Malicious software, or malware for short, is designed specifically to infiltrate and attack computers without the user’s consent. Malware can be used for various purposes: monitoring, information extraction, data destruction, ad injection, etc. It’s a catch-all term, so let’s see the main types of variants hiding behind the hood.
VIRUSES
- The originator (OG) of malware. A virus is typically a piece of computer code attached to a program or file. Once activated, it can easily replicate itself. Disruption is in their design, so once the file (e.g. an illegally copied piece of software or media) is opened, the virus can steal information, create operational issues, or delete data.
WORMS
- While viruses are attached to files, worms are standalone programs that infect whole networks. Once a worm hits a network, it can swiftly replicate itself to all devices on it. A typical example of worms is bulk emails with an infected email attachment. When infected, the computer forwards the email automatically to its network list, and so the worm spreads.
TROJAN HORSE
- Named after the story of the Trojan wooden horse, this virus always advertises itself as a desirable program, while hiding malware underneath. Often, Trojans are created to open a backdoor in the system, which hackers could later use for their gain.
SPYWARE
- The end goal for spyware, a program running in the background, is to quietly collect your sensitive information and report on your activities. Keyloggers are common examples: by logging your keystrokes, hackers can steal financial or personal data.

ADWARE
- A salesman’s best friend. This malware collects data specifically for advertisement targeting. While typically not overtly malicious, adware can also redirect you to sketchy sites, slow down your system, or even hide Trojans within.
Ransomware
- Data is gold — and hackers know it. Ransomware is designed to encrypt all data on a system without damaging it. The goal? To hold it hostage with a decryption key until a cryptocurrency payoff is executed. Huge companies and whole cities have fallen victim to this dangerous malware.

HYBRID
- As computers evolve, hackers do as well. That’s why the malware of today is usually a mixture of different variants. Because of this, you can never be 100% safe but that doesn’t mean you should drop your guard. Instead, read what steps you can take to limit your vulnerabilities.
These are few malwares I know about hope you liked the article ❤
